
Stop hiring fraud at the source
Fraudulent candidates are getting smarter—and more expensive. Deepfakes, stolen IDs, and impersonators slipping into your hiring funnel drive costs up and slow down hiring.
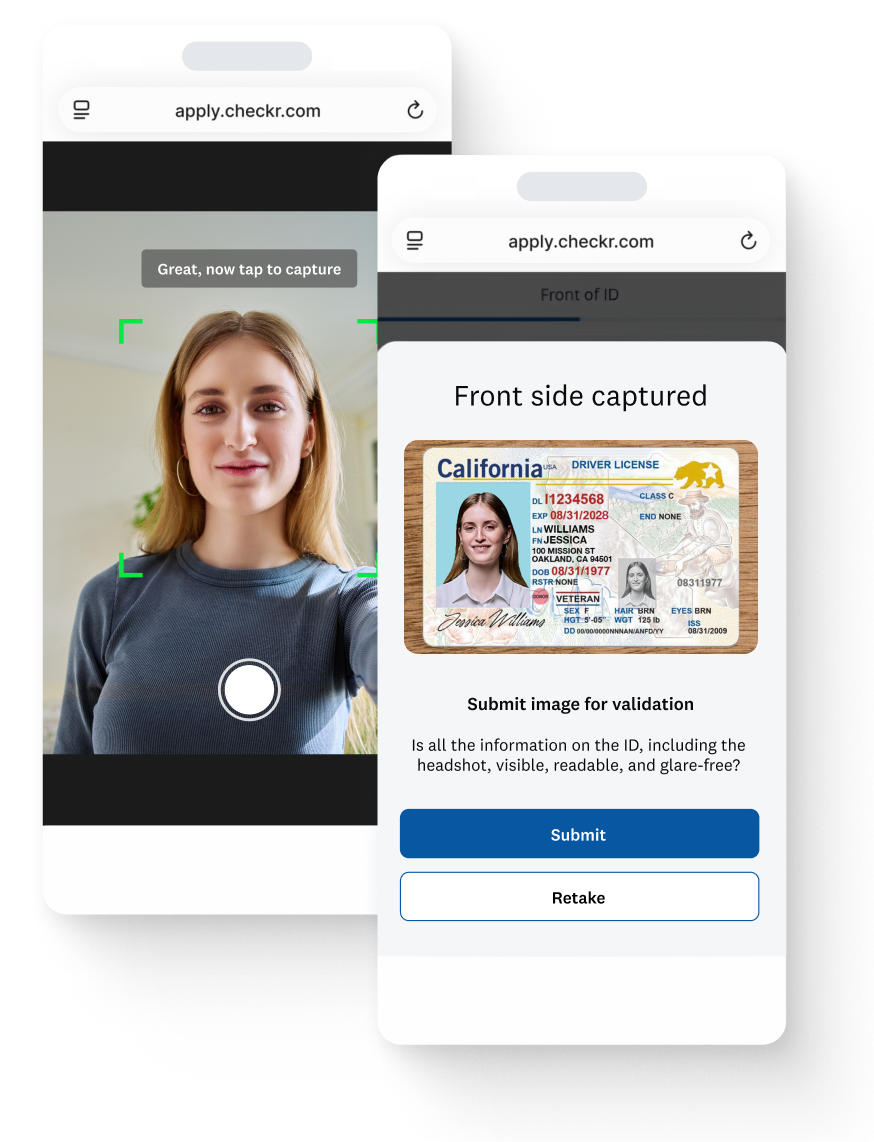
Checkr identity verification (IDV) adds a quick document and liveness check before the background check starts so you only screen real, verified candidates.
One platform, one flow
Embed IDV directly into your Checkr apply experience—no extra logins, no redirects, no drop-off, no friction. The result: Higher completion rates, less candidate confusion, and faster time to hire.
Prevent fraud where it matters most
Stop hiring fraud upfront before the background check.
Cut risk and waste
Don’t screen candidates with fake identities.
Build trust
Give compliance and people teams audit-ready proof of identity.
Future-proof your hiring
Stay ahead of evolving fraud trends with our best-in-class IDV solution.
Verification you can trust
Smooth & secure
Device fingerprinting and liveliness check verifies that the candidate you’re screening is who they say they are.
Streamlined workflow
Integrated Checkr IDV and background check flow ensures your candidate’s information matches each step of way.
Speed & simplicity
Candidates complete IDV directly from their mobile device with a few simple clicks, reducing dropoff and improving completion rates.